Underdist 3 Vulnerable VM Walkthrough
1) Initially I tried nmap to discover the open ports shown below.
2) Then I used Nikto and dirb for further enumeration.
3) Checking for port 80 gave me the following.
4) No clue left what to do next.
5) Then I tried view source and I saw the following.
6) Fetching the URL mentioned in the view-source gave me the following.
7) The url seem base64 encoding as == is present. I then decoded it and found the following.
8) Then I thought of encoding /etc/passwd in base64 format to launch LFI (Local file inclusion) attack.
I tried various payload such as /etc/passwd ../../etc/passwd finally the following payload gave me /etc/passwd file on the browser.
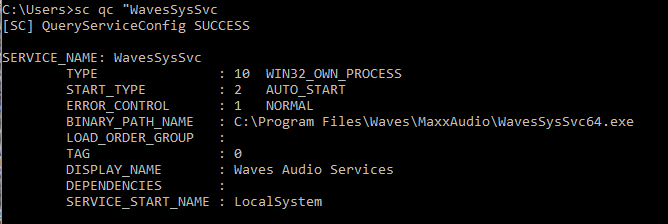
9) Then I copied the /etc/passwd file in user.txt and created a userlist file for SSH and smtp bruteforce.










Comments
Post a Comment