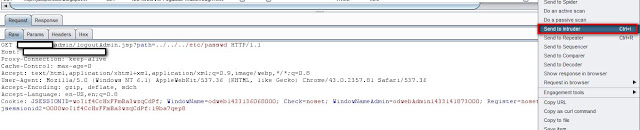
De-Ice 1.20b Walkthrough
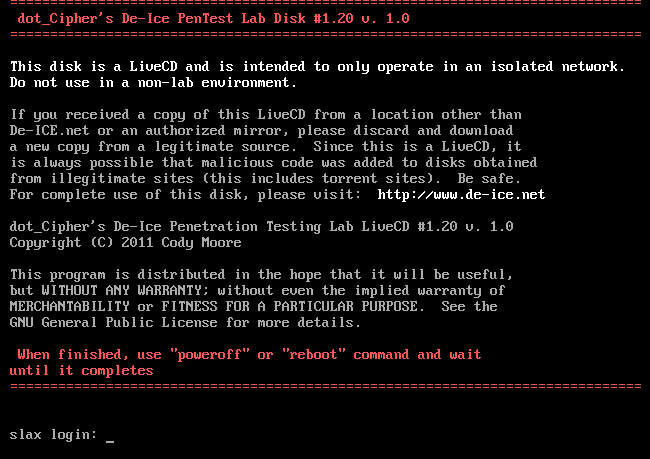
Well 15 days back I have written Walk-through of De-Ice 1.120a On My Blog . I got great response by vulnhub and they published my walk-through https://www.vulnhub.com/author/trnform3r,152/ With a such a warm encouragement I feel like writing more walk-through. Here Is my walk-through on De-Ice 1.20b. You can download the VM and get more info about it form here . Note: The attacker machine and the VM should be in the subnet of 192.168.1.0/24 Labsetup: 1 - Open Vmware - > Edit - >"Virtual Network Editor" 2 - Click on "Add Network" and add any 1 Network example VMnet2 3 - Select VMnet2 and change Subnet IP - 192.168.1.0 and Subnet mask - 255.255.255.0 also select "Host - Only" 4 - Now add this adapter VMnet2 for both the machine. When you start the VM it looks something like this.