De-Ice 1.120a Walkthrough
Few days back my friend Chetan told to get hands on De Ice and Kioptrix series before taking PWK labs.The very next weekend I started with De-Ice http://hackingdojo.com/downloads/iso/De-ICE_S1.120.iso . As my bridge network was on 192.168.1.x series I thought of doing De-Ice 1.120a just by bridging the VM. One of the awesome URL that I found today was https://blog.g0tmi1k.com/2011/03/vulnerable-by-design/ .
Enumeration:
- I started with nmap as usual to find all the open ports. I usually use version detection and aggressive scan in nmap.

- Well this anonymous thing on port 21 ftp didn't helped me and took me no where. There was also mysql port open which was not much of a use. But running few mysql related metasploit module and bruteforce using rockyou.txt would be good.
- I tried to access the server on port 80 and it gave me the following.

- It has a simple functionality of adding and viewing a product as shown below.

SQL Injection:
- Well looking at the URL, I couldn't stop myself from running SQLmap. The parameter 'id' was injection. I tried os shell and pwn with sql map but there was no permission for writing on the directories. I even tried to brute-force the writable directory but it didn't work. Moving on after some permutation and combination I used the below query to retrieve users and password hashes.
- The command ended with --users --passwords.

- Well using the username and password mentioned above I did ssh using ccoffee with the password ********.
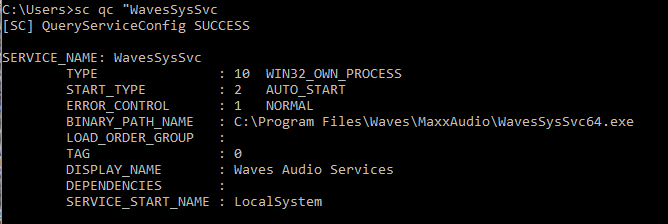
- Checking in the scripts folder I found '.sh' file which says
- Now here's the trick which took me a long time to figure out. User ccoffee can execute getlogs.sh file. So I renamed the original file as follows.










Hi Hashim,
ReplyDeleteare we allowed to use sqlmap in pwk labs??
thanks a lot for all the blogs you have put up..they have been a great help always
AH
Slot machines by casino - World Casinos
ReplyDeleteSlot machines 부들 이 벗방 are a form of casino 페이 백 먹튀 equipment used for 뱃365 gambling. in the casino section of 벳 365 한글 the video slot machines and other machines which 플레이 포커 was Rating: 5 · 5 reviews